Security management using DevOps
Safety and risk assessment are one of the most important elements subjected to cyclical inspections. In order to improve these processes, it is worth considering their automation. DevOps practices can be useful, which, according to the assumptions, bring many benefits and improve the control process in the organization.
The methodology is defined by the AWS as follows:
“DevOps is a combination of cultural philosophies, practices and tools that increase the organization’s ability to deliver applications and services at high speed: they evolve and improve products at a faster rate than organizations use in traditional software development processes and infrastructure management. This speed allows organizations to better serve customers and compete more effectively in the market. “
DevSecOps complements the practices and focuses on security issues:
“The purpose and intention of DevSecOps is to build a mentality that “everyone is responsible for security” with a view to securely separating safety decisions at a fast pace and matching those who maintain the highest level of context without sacrificing the required security.”
You can read more about DevSecOps in our blog post – DevSecOps as a security guard.
When managing security, we can use the principles that suggest DevOps practices: risk modeling and continuous integration and security assessment.
Risk modeling
An important issue on which the process of developing safety control mechanisms should begin is risk modeling.
Priority should be given to creating a risk register that contains all information about threats: their analysis, counteracting and status. On its basis, the probability of the occurrence and impact of hazards is assessed.
In order to facilitate the task, there are several tools that will certainly improve the entire process.
We can distinguish, among others:
- STRIDE – a threat model developed by Praerit Garg and Loren Kohnfelder to identify computer security threats. It provides a mnemonic for security threats in six categories: impersonation of user’s identity, manipulation, rejection, the disclosure of information, privacy violation or data leakage, D.o.S, unauthorized access.
- PASTA – a process for simulating attacks and analyzing threats is a seven-stage, risk-focused methodology.
- DREAD – this is part of the system for assessing computer security threats previously used by Microsoft (until 2008). It is currently used by OpenStack. It provides a mnemonic for security risks of risk assessment using the five categories (listed in point 1).
- VAST – the basic principle of the methodology is the need to scale the risk modelling process in the entire infrastructure and the entire SDLC and integrate it in a simple manner with the Agile software development methodology. The methodology is intended to provide practical results for the unique needs of various stakeholders: application and development architects, cybersecurity employees and senior management.
- Trike – the aim is to use threat models as a risk management tool that is used during the audit. Threat models are based on the “requirements model”. In turn, the requirements model defines the “risk level” defined by stakeholders, assigned to each class of assets. The prepared threat model is used to construct a risk model based on assets, roles, activities and calculated risk exposure.
- OCTAVE – CERT method of critical importance for threat, resources and risk assessment (OCTAVE). This is an approach to information security risk management. It was designed to be flexible enough for the organization and to meet unique and highly contextual analysis needs, thanks to customization capabilities.
In addition to the mentioned models, it is worth to read the documentation prepared by AWS – Cloud Adoption Framework, where you will find tips on the coordination of various parts of the organization, e.g. migrating data to the cloud. The CAF guidelines are divided into several areas, important for the implementation of systems based on the AWS cloud.
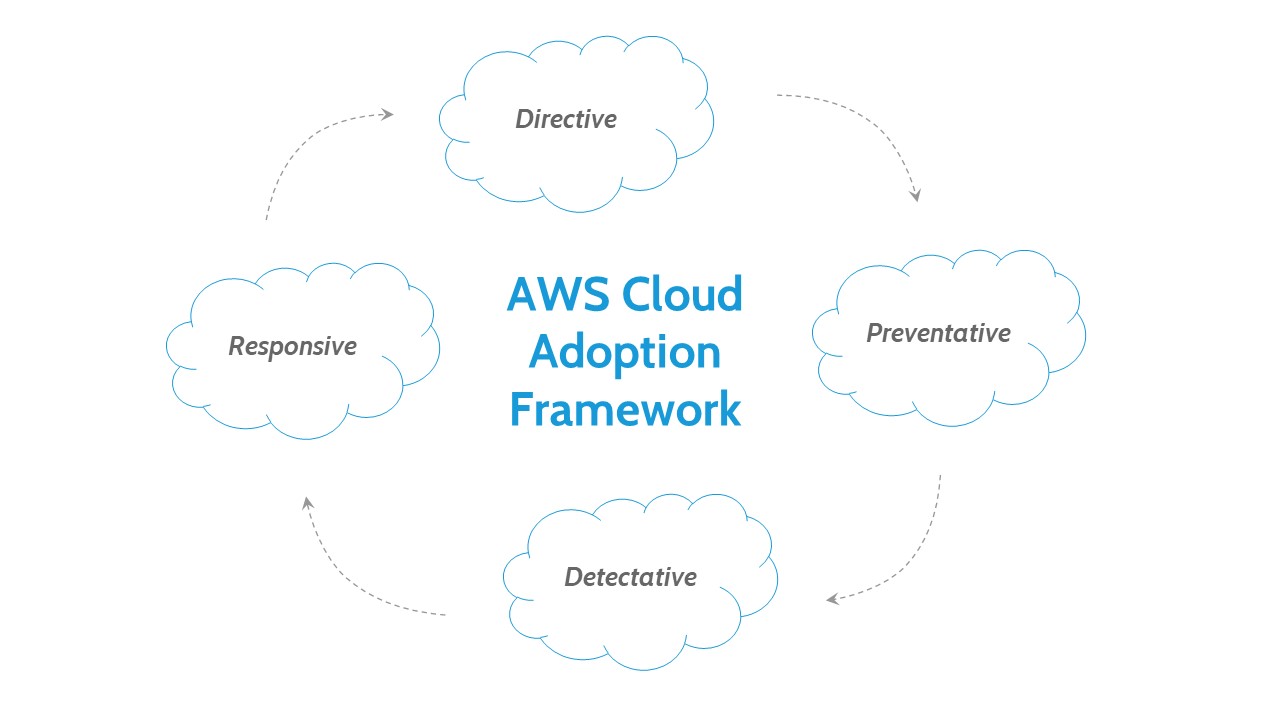
The adoption scheme of the AWS Cloud Adoption Framework
The guidelines aim to improve and ensure the proper development of security controls. Every regulation should be carefully formulated to avoid ambiguity. It usually has a form of a single instruction requiring some action or configuration. The tips mean that the risk is documented or completely eliminated. There is also some residual risk that can be managed further by using other security controls. Full documentation about the CAF can be found here.
Continuous integration and security assessment
Once the security controls have been created, you can go to the next stage. It is the creation of a scenario of acceptance criteria for users’ actions, which then undergo a test of the correctness of operation. After the test, we enter the remaining criteria as rules into the AWS Config service, allowing for continuous evaluation of the entire AWS account in terms of compliance. As a rule, compliance with the control rules based on the time segment (<15 min) is assessed. The defined elements can be placed in the CI / CD Pipeline, thanks to which security controls will be as fast as the rate of innovation in the DevOps process.
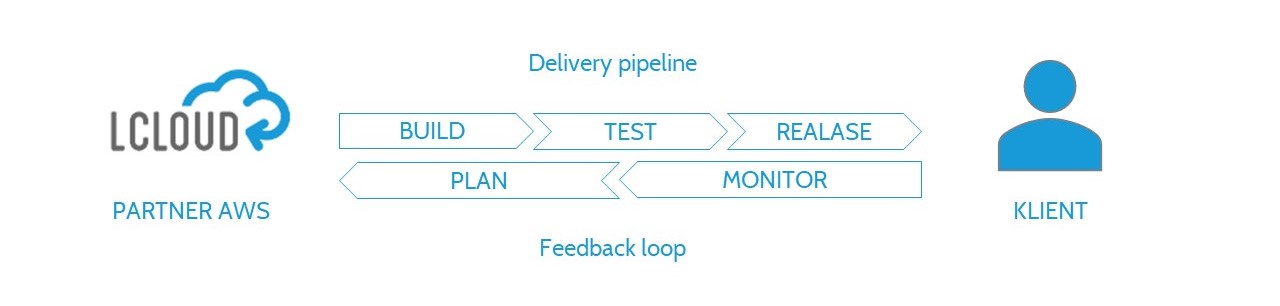
Diagram of the standard DevOps pipeline
Advantages of the applied solution
The use of the DevOps approach in security management brings a number of benefits:
- In contrast to the traditional approach (audit), continuity of integration and security assessment, allows you to be consistent with the requirements / legal regulations at all times.
- In order to save time for labour-intensive audits, it is worth using the AWS Config service.
- Easy access to its panel, allows you to quickly launch simple operating procedures.
- We receive immediate information on the compliance of our activities with our control rules, and thus with legal regulations.
- Developers receive feedback on the proposed solutions in advance.
 AWS pays attention to keep the division between risk proofs and risk management processes. Exceptions that appear in the code are difficult management cases and may give a distorted assessment of resource compliance.
AWS pays attention to keep the division between risk proofs and risk management processes. Exceptions that appear in the code are difficult management cases and may give a distorted assessment of resource compliance.
Cloud solutions are slowly starting to become popular. Therefore, the technological development of other components complementary to cloud computing is extremely important. The DevOps practices allow for fast and efficient creation of solutions, with a high level of security.
