Security and compliance based on the AWS cloud
Amazon Web Services as a cloud leader for more than 12 years and creating new solutions, has also developed a number of audit procedures that are aimed at ensuring compliance with restrictive criteria, in many demanding industries.
An important issue that we should remember from the outset is Shared Responsibility. The diagram below shows who is responsible for particular areas, using cloud solutions. On the client’s side remain data protection, access management, network and firewall supervision. AWS, in turn, takes responsibility for basic services such as compute, database services, network connectivity or data storage. In addition, AWS is responsible for the availability of regions and the operation of accessibility zones (Availability Zones), including end (edge) locations.
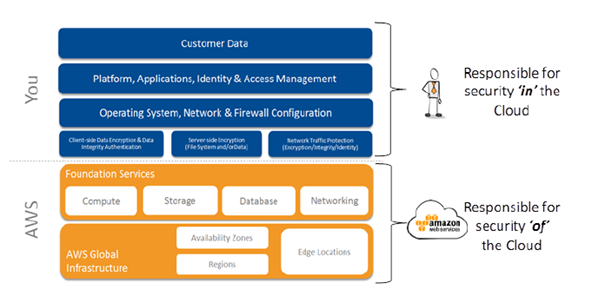
Source: Introduction to Auditing the Use of AWS
Being aware of the security foundations in the cloud, the next step is to identify the client’s assets placed in the AWS. Depending on your needs, these can be:
- EC2 instances,
- data warehouses,
- apps,
- or simply data.
Basically, there is no major difference in the categorization of resources stored in the public cloud, and those that the customer stores in his own data centre. AWS gives the resources 2 unique identification numbers: the first number is the AWS account number; the second is ARN (Amazon Resources Names), which is necessary when you need to clearly specify a given resource in services such as Amazon RDS, API Gateway, or IAM. In addition, each of the AWS services creates its internal identifier, which can be helpful in cataloguing the environment’s resources.
Proper management of resources allows for setting the aim and direction of security implementation. The essence is to check which procedures, rules and plans can be applied to used AWS services. As part of the management, it is crucial to determine who in the organization manages the AWS account and who is the owner of the resources maintained under the account, and lastly who manages the services that are used.
Configuration and proper management of resources must be preceded by an in-depth analysis of the categories of used resources. It is important to safely configure the system and applications (taking care of safe configuration settings and protection against malware) and controlling changes taking place in the resources. It is also important to properly manage the risks resulting from emerging security gaps to protect the stability and integrity of the resources.

Another extremely important point, verified during the audit, is security recording and monitoring. This is primarily about logs, in which all behaviours and events appearing in user’s systems and networks are registered.
During logical access control, the most important aspect is determining who or what can have access to a specific resource, as well as the type of actions that can be performed on a given resource. As part of the audit, users should confirm the authorization to perform specific functions or access to resources.
The next aspect is related to the previously mentioned monitoring. Referring also to the issue of shared responsibility in the cloud – both the AWS client and the AWS itself are obliged to respond to incidents related to threats. The main area of the audit is the assessment of the effectiveness of the existing incident management control.
Another important action is data encryption. It is necessary if they are confidential. Currently, Amazon S3 provides an automated encryption service. It is worth paying attention to data encryption at rest as well as in transport. This is just as important as protecting data stored locally on disks. It should be mentioned that many security policies call into question the Internet as a secured communication medium.
In the case of unsecured data and their loss or failure, the Disaster Recovery process becomes a major issue. Thanks to the solutions provided by AWS, it is possible to design resistant and quickly responding systems to incidents of applications. It is important to ensure that the systems are configured to use multiple regions and Availability Zones during the design process. This will ensure high availability and fast recovery time.
Network management in the cloud is very similar to managing it in an on-premise model. The only difference is the components (e.g. firewall) that are virtual in the cloud. It is the customer’s responsibility to ensure that the network architecture complies with the security requirements of his organization. Improper configuration of external security may cause many threats. In order to verify the correctness, it is worth using the AWS Trusted Advisor.

It is also worth paying attention to the security features, that AWS uses in the case of its Data Centers. Physical access is strictly controlled both on the outskirts of the land on which the building is located and also at the entry points to the facility. They are controlled by professional security guards using video surveillance, intrusion detection systems and other electronic tools. Both authorized AWS employees and outsiders must undergo a two-step control to access individual floors of the data centre. All visitors and contractors who gain access to zones are required to provide proof of identity. Their data is placed in registers, and moving around the building takes place in the escort of security guards.
In summary, specially designed AWS tools were created to help maximize the protection of AWS cloud users’ data and applications. In addition, through the systematic conduct of audit activities, an unbiased and objective opinion can be obtained regarding the actual state of the audited areas. They will also confirm the compliance of organizations and elements with the provisions of legal or normative regulations. They will also allow optimizing financial outlays incurred to secure systems. They will also strengthen awareness of AWS security solutions.
Security and compliance – this is one of the services during which we undertake a number of activities at LCloud, whose overriding goal is to ensure full security of all resources. We also put our SlideShare on security in the cloud, which you will find under this link.
