DevSecOps as a security guard
There are many approaches to managing IT projects. One of them is DevOps, also used in working with the AWS cloud. DevOps is, in short, a technique combining the development and exploitation of resources, which aims to provide the highest quality of cooperation between IT maintenance specialists and software development specialists. This methodology is based on the iterative work model, which is based on repeatability (iteration) and the fastest possible delivery of the solution (code) in the shortest possible time. The term DevOps was first used in 2009 by Patrick Debois during DevOpsDays in Ghent.
So what the DevSecOps is?
The safety element is now included in the already known DevOps methodology. Already at the stage of creating an IT solution, a security engineer is additionally included in the operation. A person or department dealing with security who, in consultation with developers and the IT maintenance department, consults the code that they co-create and implement. This allows you to eliminate gaps in the code, which are an easy morsel for hackers. To better illustrate the operation of the mechanism, the following diagram shows how important it is to integrate the DevOps approach with the appropriate level of security.
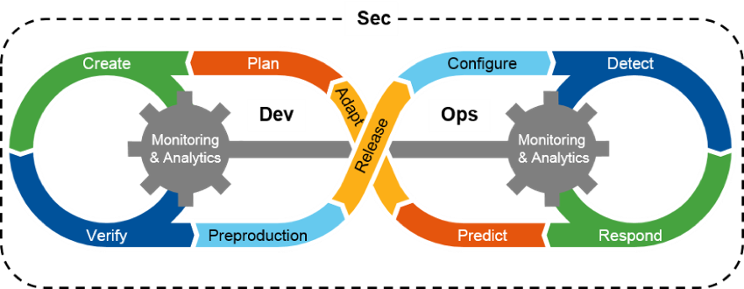
Source: “DevSecOps: How to Seamlessly Integrate Security Into DevOps”, Gartner, 2016
During the implementation of individual activities such as: planning, creation or implementation; the factor connecting the work of both departments is knowledge of secure coding (secure software engineering).
DevOps is undeniably a methodology that has improved the work on implementing and adapting solutions. First of all, including large companies, where tens or hundreds of deployments are carried out in a short time. On the other hand, adding a security layer in DevSecOps allows for faster verification of created codes and repairing or complete elimination of created errors / security gaps.
The DevSecOps methodology clearly puts emphasis on the security layer. That is why it has found its application in the financial and telecommunications industries, as well as in the development of advanced applications. During the preparation of the solution, protection and security should focus, for example, on permission control or protection against malware. Threat awareness allows for more effective work of programmers and problem-free maintenance of the solution.
In the further part of the article there are a few tips that will help in the application of the DevSecOps methodology.
As part of automation, the DevOps methodology helps in deploying applications, scaling resources, ensuring high availability of applications and the environment, creating backup copies and implementing changes in security mechanisms. The first step should be to define the goal to be achieved. Then, you should indicate the security checkpoints that are necessary to maintain its highest level. As a result, a targeted variant of the use of automation can be created.
Another activity is to understand the possibility of using codes under an open source licence. Solutions based on the cloud and DevOps methodologies allow for more efficient creation of new applications using ready-made code fragments. When using the source code used to create a new application, the question becomes whether it does not create a contextual gap. Thanks to the services prepared by AWS, you can solve these problems in an easy and effective way. In this case, the Amazon Inspector service will apply, which automatically evaluates applications for weak points or deviations.
Important in the DevSecOps methodology is the selection of appropriate SAST (Source Application Security Testing) tools. At the beginning, it is worth considering the inclusion of capture rules such as errors in SQL. At the moment when people working with the code see how the tool will allow them to catch security gaps during work – they will be more willing to use it.
Hazard modeling and risk assessment are also important. They are not the simplest activities. That is why it is worth paying attention to them before we start using the DevSecOps methodology. Each risk assessment method includes common elements. These include: identifying threats, assessing the probability of potential threats and losses they may bring. Thanks to practice connected with risk assessment and models of threats, people involved in security can get a better idea of, among others, about attacks and their types, confidential data and their control mechanisms etc.
More tips on good practices on the use of the DevSecOps methodology can be found in the presentation available on SlideShare.
DevSecOps Best Practices from LCloud
- effectiveness of threat detection
- high security
- cost reduction
- the speed of the solution provided
All the above-mentioned advantages have an impact on the company’s reputation and improvement of the existing business model. An important factor in the practical application of the methodology based on agile solutions is the fact in which it is worth analyzing inputs and their estimation during projects. Estimation is not a precise tool, but only an approximate measure of the workload devoted to the solution being prepared. The justification is in the fundamentals of the Agile methodology, which is based on empirical process control. It involves frequent inspection and adaptation of activities. These procedures carried out on an ongoing basis allow for the location and correcting of wrong decisions, elimination of obstacles and inaccuracies resulting from the fact that there is a variable and unpredictable reality in which the software / application development process takes place.
When undertaking a project, it is worth considering using the DevSecOps methodology. It gives not only the possibility of a safe process of creating new solutions, but also allows for a more effective and faster implementation.
If you have questions related to DevSecOps or you are interested in the issue of security, contact us!
