How to effectively implement the Shared Responsibility model and strengthen data security?
Choosing cloud computing means opting for a high level of security. However, this does not mean that full responsibility for overall Security lies with the cloud service provider. That is why it is worth explaining what the Shared Responsibility Model is and how to work on strengthening the security of cloud infrastructure.
Data is currently the most valuable asset for many organizations. Loss of its confidentiality, integrity, or availability can lead to financial losses, reputational damage, and even legal issues. Data security in the cloud therefore includes protection against unauthorized access, hacking attacks, misconfigurations, as well as failures and data loss.
What is the Shared Responsibility Model?
The shared responsibility model is a concept in which security and compliance in the AWS cloud environment are divided between the service provider (AWS) and the customer. Responsibility for managing specific IT elements depends on both the scope of services used and the way they are integrated into the organization’s infrastructure, as well as applicable legal regulations.
According to this model, AWS is responsible for the security of the cloud infrastructure – from the physical layer, through host operating systems and the virtualization layer, to the protection of data centers. The customer, on the other hand, manages their application environment, guest operating system (including updates and security patches), as well as firewall configuration and additional protection tools such as encryption or key management.
Shared responsibility also applies to IT control mechanisms. AWS implements and supervises controls related to the physical infrastructure, while the customer can use AWS documentation to assess and confirm the effectiveness of safeguards implemented in their infrastructure. This makes it possible to take industry requirements into account and maintain a high level of security and compliance of business processes.
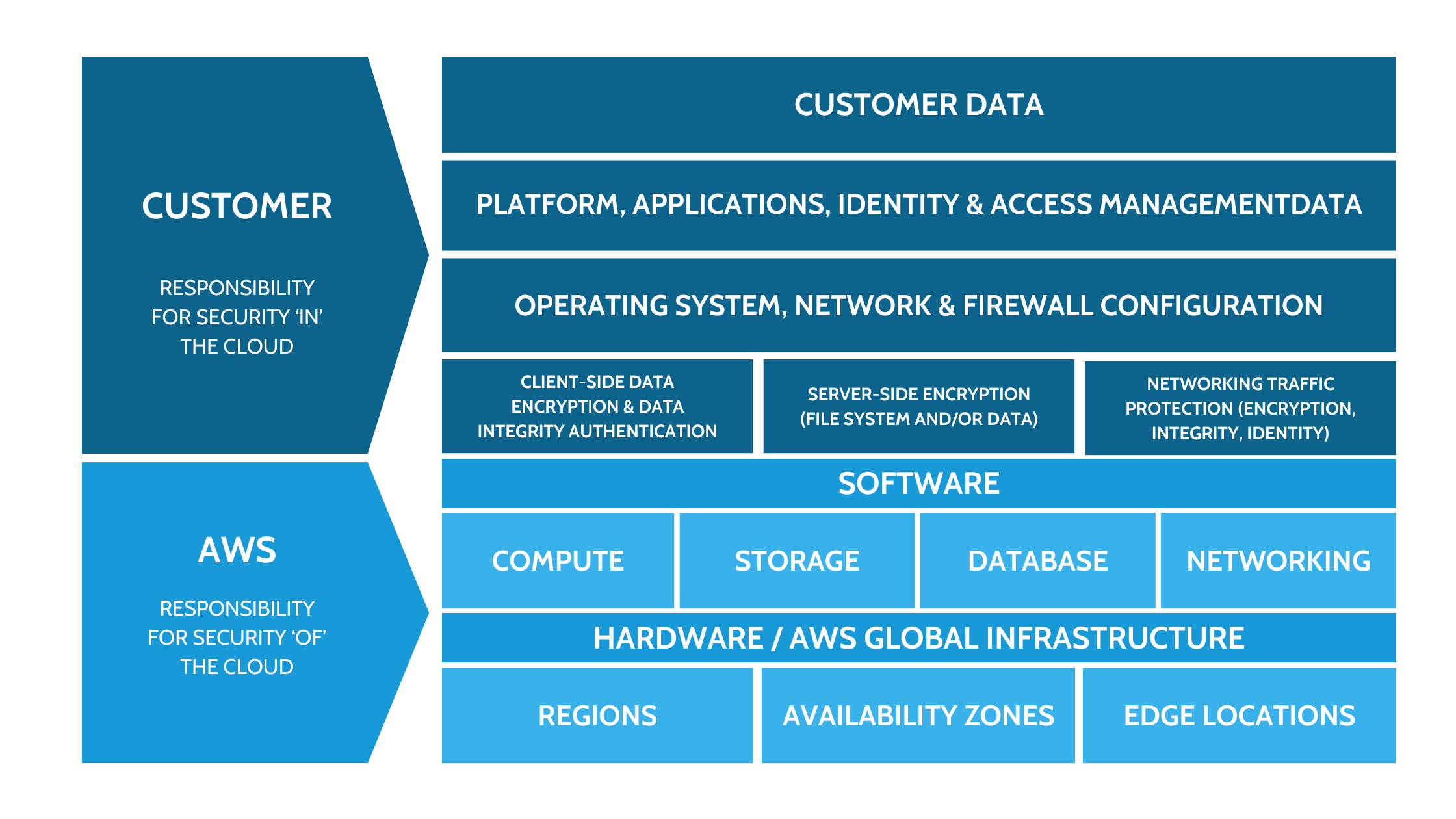
Effective risk and compliance management in AWS Cloud requires not only implementing technical mechanisms but also understanding how to apply the principles of the Shared Responsibility model and consistently strengthening data security.
Importantly, a formal approach to risk assessment in cloud implementations begins with precisely defining requirements and analyzing possible threats to all layers of the cloud environment, both on the AWS and customer side.
Security in the cloud – how to manage risk and create a plan for its reduction and threat response?
The first step in risk management is systematically identifying and assessing potential threats and defining the most important assets and processes requiring protection. Based on this, appropriate control measures should be implemented, such as data encryption, access policies, automated monitoring and alerting mechanisms, as well as regular audits of the environment configuration. Regular audits, activity monitoring, and implementation of automated control mechanisms make it possible to detect and minimize risks before they threaten data integrity or confidentiality. Equally important are continuous analysis of AWS compliance documentation and evaluating internal processes against current legal regulations and industry guidelines.
An organization using Amazon Web Services should clearly define which aspects of security fall under its responsibility, such as guest operating system updates, application configuration, or managing permissions and encryption keys. AWS, in turn, ensures the security of the infrastructure, physical layer, virtualization, and hosts.
An important element of the risk reduction plan is defining incident response procedures, including detection, reporting, quick mitigation of security breaches, restoring system functionality, and internal and external communication. It is extremely important to test these procedures, for example by simulating attacks or failures, to ensure that the plan works effectively in practice.
The organization should also regularly update its plan in response to changing regulations, industry requirements, and evolving threats. AWS documentation, audit reports, and compliance management tools (e.g., AWS Artifact) help not only meet formal requirements but also draw conclusions and continuously raise the level of cloud security.
How to strengthen data security in AWS Cloud?
To effectively increase the level of protection, organizations should use data encryption both at rest and in transit, implement access policies based on the principle of least privilege, and use multi-factor authentication. It is also important to define roles and processes related to access control, as well as to conduct regular tests and audits of cloud environment configurations.
Automation plays an increasingly important role in this context, eliminating the risk of human error – tools based on artificial intelligence and machine learning help detect anomalies, unauthorized access attempts, or unusual activity, enabling faster responses to potential incidents. Equally important is building a culture of cybersecurity within the organization, including regular employee training and clear communication of data protection procedures in the cloud. AWS actively supports customers in this regard by providing tools for risk management, automated control and compliance, as well as reports from independent audits confirming compliance with international standards. These are available in the AWS Artifact portal. Among the key services worth mentioning are:
- AWS GuardDuty, which provides continuous monitoring and analysis of events for threats,
- AWS Shield Advanced – a service dedicated to advanced protection against DDoS attacks,
- Amazon Macie supporting classification and protection of sensitive data,
- AWS Security Hub integrating multiple sources of information and enabling consistent incident management.
It is also worth mentioning AWS WAF, the web application firewall, which helps protect services against the most common types of network attacks. A fully utilized Shared Responsibility model means not only meeting regulatory requirements but also strengthening the company’s competitiveness through a high level of information protection, process transparency, and the ability to dynamically respond to new types of cyber threats.
Summary
As can be seen, by choosing cloud computing, we adopt the Shared Responsibility Model, where risk is a shared responsibility of the customer and the cloud service provider. However, this does not mean that AWS leaves customers without proper tools – Amazon Web Services is also a huge set of services focused on security and compliance, which greatly help in managing risk and adhering to established standards.
Migration to cloud computing is a huge step in the digital transformation plan, but its execution requires a professional approach. Contact our specialists and open up to modern cloud services today! Write to us at kontakt@lcloud.pl
